Collins Dictionary defines a framework as a particular set of rules, ideas, or beliefs that are used to deal with problems or to decide what to do. In the case of cybersecurity, the National Institute of Standards and Technologies define a cybersecurity framework as a risk-based approach to reducing cybersecurity risk composed of three parts: the Framework Core, the Framework Profile, and the Framework Implementation Tiers.
FutureCISO spoke to Richard Howe, chief technology officer for ASEAN with Kyndryl for his take on the importance of cybersecurity frameworks, and how CISO can adapt such into their security practice.
When it comes to security framework adoption and compliance in Singapore and the ASEAN region, what are organisations getting right?
Richard Howe: In Singapore and the ASEAN region, organisations are recognising the necessity of comprehensive security frameworks. Many are referring to globally recognised standards such as ISO/IEC 27001 and the NIST Cybersecurity Framework, which provide robust guidelines for security and enhancing cyber resilience.
Businesses are also increasingly integrating these frameworks into broader business strategies, demonstrating an understanding of security compliance, and working towards achieving resilience, which is critical to sustaining operations and protecting assets in an increasingly digital landscape.
In which area do they falter: framework development, execution, enforcement?
Richard Howe: Despite these successes, organisations may face challenges in executing and enforcing these frameworks. While development might be thorough, the practical implementation can be hindered by resource limitations, a lack of skilled employees, or poor coordination across departments.
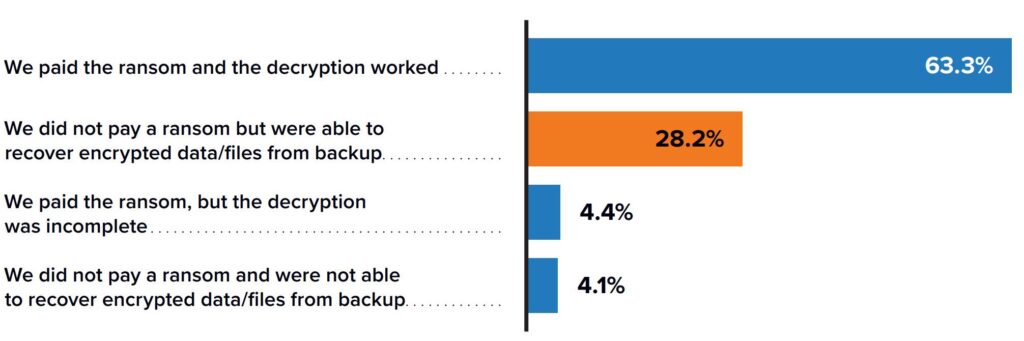
A study by IDC found that few organisations can recover on their own. Among respondents, 28.2% indicated they avoided paying a ransom because they were able to recover using their backup systems, 67.7% resorted to paying the ransom, and most of them reported that their decryption key worked. Unfortunately, 4.4% paid the ransom but couldn’t decrypt their data.
Figure 1: Recovery rates for paying or not paying the ransom
There is also a lack of resiliency planning after execution to ensure enforcement. Many companies have security response retainers, allowing them to test policies they have in place and respond in the event of a security incident. However, those retainers would not be able to help with recovery after a breach.
Oftentimes, security policies are not standardised and uniform across the organisation, which can lead to vulnerabilities that undermine the overall security infrastructure. This adds to the challenge and currently, having consistent adherence across all levels of the organisation remains a critical gap.
How can the CISO/leadership ensure that the security framework is aligned with the organisation’s unique risk profile and business objectives?
Richard Howe: To ensure that the security framework is aligned with the organisation's unique risk profile and business objectives, the CISO/leadership should:
- The importance of the security framework and its relevance to protecting the organisation needs to be understood at the board level. The impact on reputational and organisational risks are board-level concerns. Ensuring the buy-in at this level will drive support through all layers of the organisation.
- Determine the company’s vision for its risk management across the organisation. This helps to unify the various stakeholders to work towards successful alignment to the framework.
- Conduct a comprehensive risk assessment to identify potential threats, vulnerabilities, and their impact on the organisation's operations and assets.
- Involve key stakeholders from various business units to understand their specific requirements and priorities. This also helps to build awareness and engage them in the process from the start.
- Tailor the security framework to address the identified risks and align with the organisation's overall business strategy and objectives.
- Regularly review and update the framework to adapt to changing business needs and evolving cyber threats.
These steps help to put organisations on a better footing to align the security framework throughout the organisation.
What should the security team do to better communicate the importance of the security framework?
Richard Howe: Beyond senior leadership and board buy-in, educating all key stakeholders about the importance of the security framework is crucial. For example, while many security teams undertake educational initiatives, these efforts can often be sporadic or not sufficiently tailored to the needs of different stakeholders.

"Having a more structured and continuous approach can be useful for the organisation, such as role-specific training programs, regular updates on emerging threats, and practical workshops that underscore the real-world impact of security measures. Additionally, building a culture of security awareness at every level of the organisation would be crucial for effective framework adoption."
These would help to convey a clear communication of the framework's objectives and benefits, and their roles in its implementation. By involving stakeholders in the framework development process, it helps to foster a sense of ownership and understanding.
How should leadership approach implementing the NEW framework?
Richard Howe: When planning to modernise the company’s security framework to align with regulatory requirements, a phased approach is generally more effective than a big-bang implementation. This allows for incremental changes that can be monitored and adjusted as needed based on priorities, reducing the risk of disruption.
A phased approach allows for:
- Gradual integration of new processes and technologies, minimising disruptions to ongoing operations.
- Pilot testing and iterative improvements based on feedback and lessons learned.
- Proper training and change management for stakeholders to adapt to the new framework.
- Ongoing review and transformation of the security policies is key.
That said, a big bang approach may be necessary in certain situations, such as when facing imminent regulatory deadlines or significant security breaches that require immediate action.
Besides modernising the security framework, organisations should also consider a broader modernisation, such as a mainframe modernisation.
Organisations might be working on legacy technologies that have older security frameworks, and by adopting a broader modernisation journey, they can be more agile and ensure better alignment with the current environment and needs.
Any best practices for measuring the effectiveness of the framework?
Richard Howe: Measuring the effectiveness of the cyber resiliency framework starts with a good security policy implemented. The framework can then be measured across several methods, including setting key performance indicators (KPIs) such as incident response times, compliance rates, and the number of security incidents detected should be monitored regularly.
Organisations can also consider conducting regular audits and assessments to evaluate the framework's implementation and identify areas for improvement, as well as detect and analyse security incidents, breaches, and their impact to assess the framework's ability to prevent and respond to threats and recover effectively.
Any best practices for ensuring the framework evolves with changing threats and technologies?
Richard Howe: In today’s digitally enabled commercial organisation, organisations, both businesses and the public sector, may find themselves constrained by ageing systems within increasingly complex environments that make protecting the enterprise challenging. Thus, preparedness is key.
Ensuring that the security framework evolves with changing threats and technologies requires a proactive and adaptive approach. Organisations would need to be ready to regularly update the framework to reflect the latest threat intelligence and technological advancements.
To ensure the security framework evolves with changing threats and technologies, organisations should:
- Continuously monitor and analyse cyber threat intelligence and emerging technologies.
- Participate in industry forums, conferences, and knowledge-sharing platforms to stay informed about best practices and emerging trends.
- Allocate resources for ongoing research, development, and training to enhance the framework's capabilities.
These three steps can help the organisation thoroughly understand the critical systems that keep the business running. They must prioritise their most important business services — including technology assets and data that powers them — and review their management plan and strategy to ensure it is adequate to mitigate each risk.
Organisations can then look at establishing a regular review and update cycle for the framework, involving relevant stakeholders and subject matter experts. They can consider leveraging advanced technologies such as AI and machine learning to enhance the ability to detect and respond to emerging threats swiftly.
In addition, having a governance framework that includes continuous monitoring, regular reviews, and compliance checks can help to ensure that the framework remains current and effective, especially if it operates across markets since security requirements vary.


