Gartner is benchmarking these cyber business value metrics that change the way organisations measure, report and invest in cybersecurity. These 16 metrics will transform how you discuss cybersecurity with your board of directors.
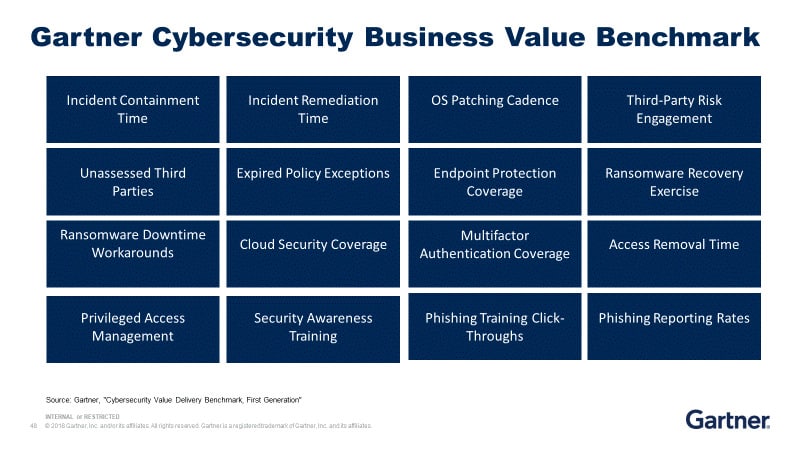
Organisations can use the information supplied here to build better metrics to guide investment and report to their board on cybersecurity.
Gartner clients have access to more detail to produce benchmarkable data like scoping guidance, definitions, and calculations.
This is an example of a full Gartner definition. Notice that this is not rocket science. The fields like target questions, in-scope elements, clock (for time-based metrics), definitions, and calculations are critical elements. It is recommended that you create a full definition like this for every metric you have.
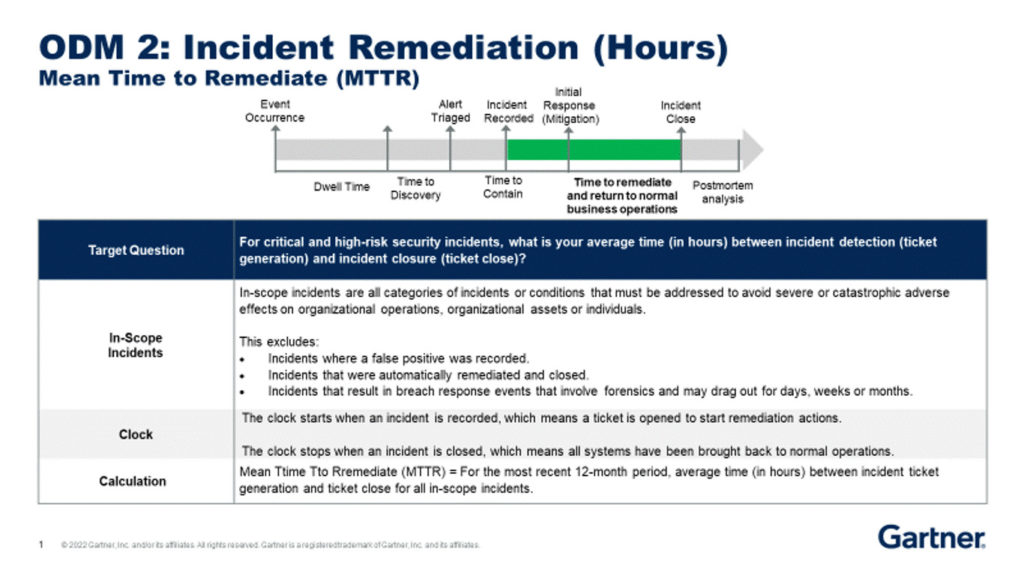
Bluntly, if you don’t have a calculation, you have nothing. The dreams of many aspiring metrics crash upon the rocks of reality when you don’t have a calculation. While I’m not supplying the Gartner calculation… you’ll be OK. There are many appropriate ways to do a calculation and I gave you an example above.
Outcome-driven metrics
Our recommended metrics are based on the Gartner construct of an outcome-driven metric (ODM). ODMs measure the outcomes of security investments.
For example, incident remediation is an ODM that measures the outcomes of your investment in response capabilities.
ODMs are explainable to executives with no technical background, they measure protection levels, and they act as value levers.
Collectively these properties change how we measure, report, and invest in security.
ODMs are easily explainable to executives
Incident remediation measures the amount of time it takes our organisation to stop hacking incidents and return the organisation to normal business operations.
This is the amount of time that an incident can spread, do damage, and lock up systems.
ODMs measure protection levels
When an ODM improves, the investment is producing measurably better protection.
When the metric degrades, the investment is producing measurably lower protection.
Remediating incidents in 16 hours is better protection than remediating in 30 hours. Because your incidents are around for 14 more hours to do damage.
ODMs act as value levers to support direct investment
ODMs support direct investment to change a protection level.
If you are currently remediating incidents in 30 hours, you can make a direct investment in getting down to 16 hours and you will be measurably better protected.
ODMs enable cyber governance based on value and cost
ODMs support choices that balance protection levels against cost.
For example, you can spend more money, remediate incidents faster, and you will be measurably better protected.
Or, you can save some money, remediate incidents slower, and you will be measurably less protected. But you will save some money.
Why did we pick these 16?
This list was built in collaboration with Gartner Research Board, which is comprised of some of the world’s largest, well-funded organisations. However, these metrics are scalable to very small organisations. None of the metrics are complex.
These 16 were selected as our first generation because they have 2 very special qualities:
First, each of these can be explained to a business executive with no technical background.
Second, they represent high-value, common security control investments. Everyone needs these.
This collection of metrics is not MECE (mutually exclusive, collectively exhaustive). You will need other metrics, but these should also follow the construct of outcome-driven metrics.
Gartner has a catalogue of 130 ODMs across 20 different control investments. You can build an ODM out of any cyber investment.
Implementing these 16 metrics
To gain full value, an organisation should instrument their systems and processes to gather these metrics continuously. “Continuous” is different depending on the metric. Some change daily, and some change once a year.
Step 1: Prioritise the metrics that are easiest to gather data and highest value.
Step 2: Use the sample above to define the scope, calculation, and required investment to gather the data.
Step 3: Make investments to gather continuously.
Step 4: Measure what you are delivering today.
Step 5: Use the data in board presentations and drive investments to achieve desired protection levels.
Benchmarking and a cybersecurity standard of due care
If you join our ecosystem and measure these 16 as we specifically define them, you will be able to compare yourself to your peers.
When you are in line with your peers, you can create stakeholder defensibility with your customers, shareholders, and regulators.
Stakeholder defensibility and benchmarked ODMs hold the promise of creating a standard of due care for security protection.
We aren’t there yet, but the first step for you is to start measuring ODMs and create a new conversation with your board.
First published on Gartner Blog Network